Vulnerability Assessment & Hardening
A full evaluation of your infrastructure, servers, and applications to uncover security gaps, outdated components, and misconfigurations. Ideal for organizations wanting to strengthen their security posture proactively before vulnerabilities are exploited.
Automated and manual vulnerability scanning of network and application assets.
Validation of findings to remove false positives and ensure accuracy.
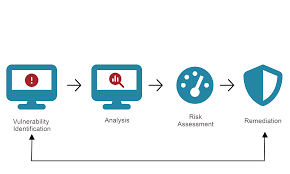
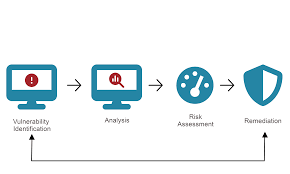
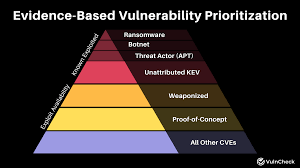
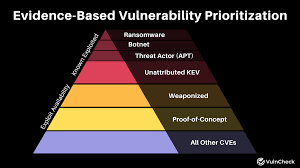
Prioritization of vulnerabilities based on risk, exploitability, and business impact.
Guided hardening sessions to secure operating systems, web servers, databases, and cloud environments.
Alignment with industry benchmarks such as CIS, NIST, and OWASP standards.




Deliverables
Verified vulnerability report with clear findings
Prioritized remediation roadmap for IT/DevOps
Hardening checklist with configuration fixes
Optional re-test to confirm remediation

Empowering potential through collaboration and innovation.
© 2025. All rights reserved.
