Security Operations Monitoring
From consulting and strategy development to implementation and support, our comprehensive services can help your business thrive.
24×7 log collection and correlation from servers, endpoints, firewalls, and cloud services.
Detection of anomalies, suspicious behavior, and policy violations using SIEM tools.


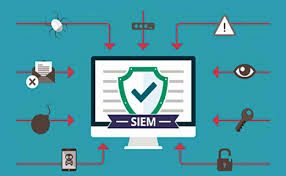
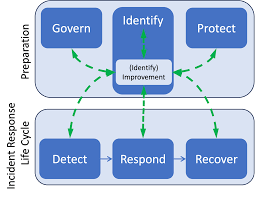
Incident triage, alert validation, and escalation based on predefined playbooks.
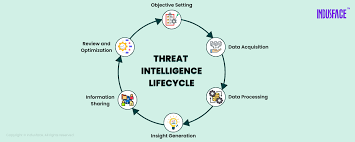
Threat intelligence integration to identify known and emerging attack patterns.
Monthly reporting on incidents, trends, and overall security posture.




Deliverables
Continuous visibility into security events and alerts
Monthly or on-demand incident reports with response guidance
Real-time notifications for high-severity threats
Post-incident review with hardening recommendations

Empowering potential through collaboration and innovation.
© 2025. All rights reserved.
